Best practices on Power BI Security
SUMMARY
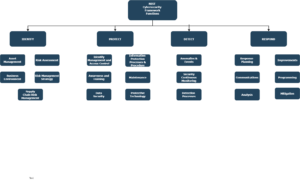
This document highlights the security features of Power BI, according to the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF). The NIST CSF is a guide for organizations to manage and reduce cybersecurity risk. Irrespective of the size of the business, the below guide will help to explain the best use of Power BI to address each category within four core actions: Identity, protect, detect, and respond.
NIST CSF FRAMEWORK:
Although the framework consists of five concurrent and continuous functions with the fifth one being “Recover”, we have aligned Power BI’s strengths and capabilities to four of the functions.
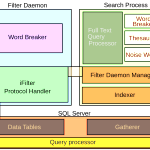
SECURITY SOLUTIONS IN POWER BI:
Power BI solutions empower users to work anywhere securely and with the tools they love. The security philosophy for the solutions builds on four building blocks with products in each block working together for organization safety.
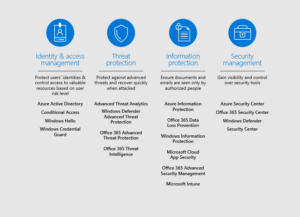
BUILDING BLOCKS:
IDENTIFY
- Synchronize Azure Active Directory (AD) to provide single sign-on for on-premises and cloud. Azure AD conditional access also creates extra layers of security and implements policies i.e.
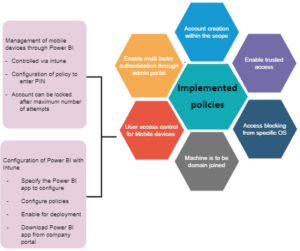
- Publish content from the Power BI desktop into workspaces in the cloud service. Colleagues adds in one of the following roles with privilege levels as a viewer, contributor, member, and admin. Access should be given depending upon roles and responsibilities as the admin role can delete the workspace and therefore, that permission should be restricted.
- Content distributes through apps. Each workspace calls as an app workspace provides the ability to neatly package all content into a single entity known as an “App”. Access can then be given to individuals, groups, and the whole company. Recipients access via the Apps menu for a read-only data visualization experience, whereas, report consumers can fully interact with the data.
- The administrative role has all the keys to Power BI work such as controlling workspaces, specifying if data can be shared externally, and limiting the ability to export data, so be selective and restrictive for its access.
PROTECT:
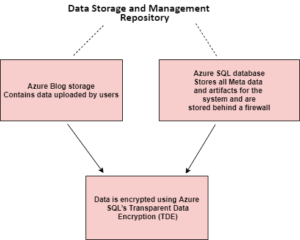
- Power BI stores datasets, reports, and dashboard tiles when data is at rest in the following manner
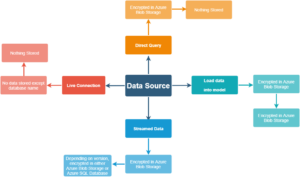
- Data request and transmittal encrypts using HTTPS to connect from the data source to Power BI
- Data caches for all data types and is also stored in Azure SQL server database
- In normal cases, Microsoft uses its own managed keys to encrypt data however, in premium, users can use its keys for that. The Content Encryption Key (CEK) used to encrypt the Microsoft Azure Blob Storage is a randomly generated 256-bit key. The Key Encryption Key (KEK) uses to then encrypt the CEK is a pre-defined 256-bit key. Always encrypted methods uses for cloud data sources.
- No data stores on the gateway and the gateway service account should not have access to data sources and gateway access limits on the service.
- Online services for Power BI require only TCP port 443 open for endpoints. Two communication protocols support i.e. AMQP 1.0-TCP + TLS and HTTPS – WebSocket over HTTPS + TLS.
- Different types of data connections determine how data is stored. For DirectQuery or Live connection, source data is not stored in Power BI except for visualization data. When data is in-process and loads into the in-memory Analysis Services database, irrespective of data connection type, the loaded data unencrypts and holds in memory for further access.
- Query caching is only available in Power BI Premium or Power BI Embedded. For Power BI reports, data for the visuals shown are cache encrypted in Azure SQL Database. Once data acts upon the Power BI service may cache the visualization data in an encrypted Azure SQL Database.
- When you connect to an Analysis Services database live connection, you have the same Row Level of Security functionality as Power BI datasets. Analysis Services Tabular and Azure Analysis Services can also apply security to entire tables and single columns within tables.
- Row-level security (RLS) provides the ability to publish the same report to your user base but exposes a different horizontal slice of data to each person. The great benefit of RLS is to avoid maintaining multiple versions of the same visualization to expose different data.
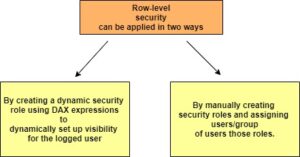
With many too Many relationship filters, propagation would not be easy. So only filtering the data based on the user will not work. To handle this scenario we have two options:

- In Power BI, the data gateway acts as a bridge between the Power BI Service and on-premises data sources. This is not defined in the gateway as it is to be defined in the dataset and these settings would not affect row-level security.
- Many developers connect to source data and publish siloed data sets in an ungoverned manner that is difficult to administrate and maintain. That is the major concern with Power BI. The solution is to create only a version depicting the truth. This approach avoids storing data in many Power BI desktop files and cloud datasets.
DETECT
- Admins and people with appropriate authority have access to the Office 365 Admin Center. This information allows you to search by date range and user. To meet regulatory and compliance requirements, audit logs use as a significant tool. The best thing is to create your custom audit or usage metrics report (Power BI Report) across the entire tenant from all workspaces. You can monitor all the activities of Power BI
- Power BI offers the facility to classify your dashboards based on categories you define. You might create labels such as Classified, Internal, Confidential, etc. All of this depends on how well you know about your sensitive data and are clear that how the legislation would affect your dashboard.
RESPOND
Response processes and procedures execute and maintain to ensure timely response to detected cybersecurity events. They are of no use if not used regularly and properly. Azure Advanced Threat Protection is designs to reduce the noise from alerts and provides only relevant and important suspicious activities. This provides an additional layer of security.